By Ismael Peña-López (@ictlogist), 01 October 2012
Main categories: ICT4D
Other tags: 15mdata, big data
No Comments »
Present: Javier Toret, Pablo Aragón and Oscar Marín, members of the group Datanalysis15M.
The research group #datanalysis15m was created to analyse the new movements that emerged in 2011: Arab Spring, Spanish Indignants, Occupy, etc. The main questions being: How can we measure augmented events? How can we measure new ways of organization, of communication, of engagement? How do ideas spread (virally)? How can we characterize network-systems?
About data
In 1969 ARPANET is born as a packet-switching network, which implies a major improvement in communications. With the World Wide Web in 1990, the user can consume information passively online with web browsers and circa 2004 the Web 2.0 is born, where the consumer also becomes a producer. All this activity is increasingly been traced and produces huge amounts of data. This is yet another evolution of the Internet which has been called Big Data.
There are many implications in the generation of such a big amount of data: privacy, security, commoditization of uses and users’ behavior, dematerialization of the economy, information overload, economics of attention, neuromarketing, etc.
Michael Cooley (Architect or Bee? distinguishes between data, information — organized data — knowledge — comprehended and applied information — and wisdom — knowledge put at the service of achieving some specific goals. Wisdom cannot be transmitted and always carries an ethical connotation.
After data acquisition, data analysis is crucial to be able to transform data into information: understanding and structuring data is the core of the information-building process. Last, but still very important, information can be presented in several ways, in what has been called information visualization.
How to organize information:
- Location: maps, dynamic maps and animations.
- Alphabet: lists of words, tag clouds.
- Time: overlapping layers of data along time (to infer correlation or even causality, depending on what comes first in time), timelines (how data evolves along time).
- Category: allows clustering of information and identification of groups.
- Hierarchy: relationships of power/importance between different sets of data.
How technology shapes moods that engage people to act. If we can tell how mood is shaped by technology — or how technology can help in mood-shaping — then technology can help in choosing the appropriate time to invite and engage people to participate.
Engagement is also related to language: the use of the 1st person of plural is much more engaging and viral rather than other alternatives. “We are”, “we can”, etc. has way more punch than “I am” or “they can”.
Network or data laws:
- First law of preferential connection: the more connections a node has, to more likely it is to gain more connections.
- Law of Metcalfe: The value of a network increases proportionally to the square of their users. Behind this law we can find the concept of critical mass: how many propagations have to take place in a network before it explodes.
- The power of histograms: while populations usually follow a normal distribution, histograms usually do not, as people lie in surveys. Thus, adjustments have to be made and caveats must be taken into account.
- Dunbar number: the cognitive number of people is circa 150. After this number, it is very difficult to have quality relationships between people. We can find that in social networking sites, even if people have several hundreds (or thousands) of acquaintances, stable relationships happen in the 100-200 contacts range.
- Power law: big head vs. long tail. Popularity, power, etc. is not evenly distributed, but distributed according to a power law/curve. This complements Pareto’s Law (20% of products represent the 80% of sales): the long tail can get thicker depending on the density of connections in the network, reaching up to 50% of the total of (in this case) sales.
- Zipf’s law: the distribution of the words in a text also follows a power law. 80% of the words in a generic text is irrelevant from a semantic point of view.
Network Analysis
Network Analysis is deeply rooted in Graph Theory models.
Types of social relationships:
- Directed: social relationship is not bi-directional
- Non-directed social relationship is bi-directional
- Explicit: relationships are explicitly stated.
- Implicit: relationships are built through data analysis.
Average distance: number of intermediaries between two different nodes as an average.
Diameter (or effective diameter) of the network is the maximum distance between the most far away nodes. The diameter usually decreases as the network increases (Leskovec, 2007).
Density: proportion of links of a network in relationship with the total of possible links.
Giant component: the biggest connected component in a network. Outside of the giant component, groups are very small.
Clustering coefficient: measures the density of connections between neighbours of a node. Probability of a connection being the connection of another connection. Clusters are linked one to another through weak ties (Granovetter, 1983). Weak ties foster serendipity: weak ties have a higher potential to expose information to their contacts that they would otherwise never discover.
Reciprocity of a directed network measures how many of these relationships are really bi-directional.
Assortativity, associated with haemophilia, is the preference for relationships between users with same or different characteristics. If assortativity (r) is bigger than zero, the network is endogamic; if r < 0, the network is dissortative. Social networking sites tend to be assortative.
Degree distribution: how connections are distributed. Networks free of scale, where a small group of nodes have a high degree of connections and a long tail of nodes with a small number of connections.
Discussion
There are different social networks that are but different layers of the same reality. The purpose of social network analysis is to try to understand one of these layers and how does a specific layer feedbacks with the rest of layers and reality. One can usually find correlations between different networks and how they sync in emotions, contents, bodies.
It is also interesting to state that we increasingly see online behaviours being translated/transposed into “real life”. Not that online networks (their composition) is replicated offline, but that the practices of sharing, communication, decentralization, etc. are also put into practice even without digital technologies, thus reshaping traditionally organized networks.
We also see how information, communications, contents in online networks transcend the platform and permeate in other (offline) media, such as newspapers or TV news. Thus, even if the former network was not significantly representative of reality, the final message does get to a significantly representative share of people.
Another aspect to take into account is, even if the users of a specific social networking site are not representative of the population, whether their behaviour can be a good proxy to predict the general behaviour of the whole population. While this might sound a contradiction (not representativeness leading to predicting the whole population), the key could be in how this sample shapes the agenda of the whole population and thus, in the short or medium term ends up being a good proxy for prediction.
By Ismael Peña-López (@ictlogist), 30 September 2012
Main categories: ICT4D
2 Comments »
Every now and then we hear about new technologies, Information and Communication Technologies or the latest gadget revolutionizing or deeply transforming institutions as we know them. Laptops will transform Education and Twitter will revolutionize democracies (and non-democracies too).
I may well be that some of these technologies or tools end up capsizing our worlds, but it is usually not so. Indeed, revolutions or transformations are a matter of attitudes, which many times can be driven by aptitudes.
Welzel, Inglehart & Klingemann describe in The theory of human development: A cross-cultural analysis three stages towards full human development:
We can consider the “objective choice” as having the appropriate resources and tools to achieve a material level of development. Or, better said, the material tier to achieve full development. New technologies, Information and Communication Technologies or the latest gadget totally fit in this category. And they might be necessary conditions, but surely not sufficient ones.
The second tier focuses in the subjective choice, that is, in wanting or being personally able to foster developmental change. Having a civic centre in your neighbourhood is to the objective choice what having the will to participate in community activities is to subjective choice. Of course, the subjective choice is strongly related with education and culture.
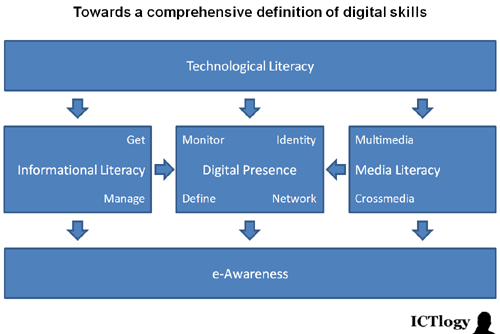
In a knowledge society, education strongly correlates with digital literacy, understood in a very broad and comprehensive manner. In From laptops to competences: bridging the digital divide in higher education I presented the following scheme to a comprehensive approach to digital literacy (and which I later put into practice in Analyzing digital literacy with a single simple tweet):
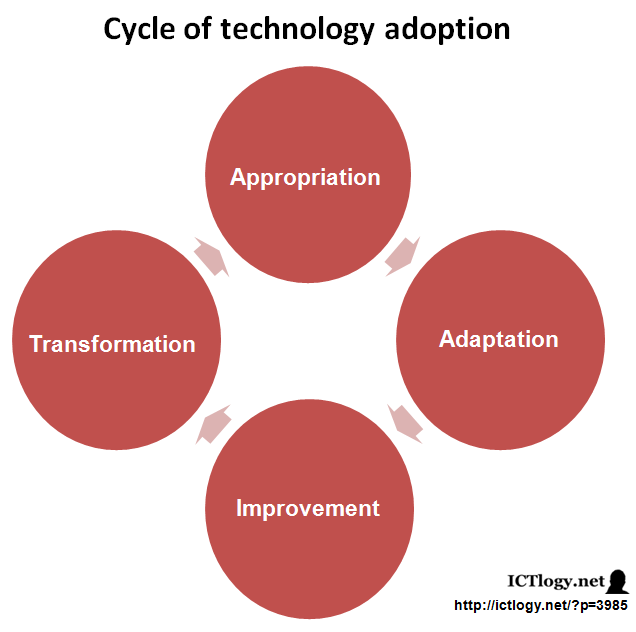
On the other hand — and as it was described in Personal Learning Environments as conscious learning strategies — we can consider four stages in the cycle of technology adoption:
Briefly put:
- Appropriation: you learn how to use the technology (e.g. you learn to write in MS Word).
- Adaptation: you substitute your old technology for the new one, but you still do the exactly same things (e.g. you get rid of you typewriter and use MS Word instead).
- Improvement: your technology allows you to perform some new tasks, or the old ones in a more efficient way (e.g. you use the track changes and commenting feature of MS Word to let others collaborate with your original document)
- Transformation: the way things worked changes radically because of technology (e.g. you use a wiki to create a collaborative document, shared online and edited in real time with videoconference support).
If we put side to side the Cycle of Technology Adoption with the comprehensive model of digital skills, we end up with quite a handy comparison:
Chance or not, the way the comparison is built shows how appropriation requires technological literacy and a little bit of informational literacy. That is, to lean how to use a specific ICT tool it does not suffice with knowing how to operate it, but also knowing its relationship with information. I know the comparison could be built in many other ways and these “conclusions” vary quite a lot, but what is shown is interesting to say the least. In this very same train of thought, adoption (getting rid of old technology) implies full informational skills plus some media literacy. When it comes to improvement, it cannot be done without taking into account that digital presence (digital identity, digital personna, etc.) is a crucial part of this new communicational landscape that a Knowledge Society is.
But we began talking about transformation of institutions by means of technology.
It should surprise anyone that transformation requires e-awareness, that is, the competence to be aware, acknowledge and understand how the world — as a whole and as your own microcosmos — is changing and will keep on changing because of the impact of Information and Communication Technologies. Without this understanding, it is almost impossible to transform anything. Without the a comprehensive awareness of the impact of ICTs it is very unlikely that one can transform anything at all (least a institution such as Education or Democracy) by means of ICTs.
Of course, there is always room for chance and luck. But the next time that it is stated that “technology X will transform Democracy” or that “the device Y will transform Education”, a necessary question should follow: does the general usage of this technology or device aligns with a full awareness of the impact of ICTs in the field? does the fosterer of such technology or device has full awareness of the impact of ICTs in the field?
Most of the times, the answers will be “no” and, thus, the specific technology or device will not be transformative. Don’t get me wrong: improvement is just great.
By Ismael Peña-López (@ictlogist), 31 August 2012
Main categories: Education & e-Learning
Other tags: mko, ple, vygotsky, zone of proximal development, zpd
23 Comments »
Developmental psychologist Lev Vygotsky defined what the person or a student can do — or the problems they can solve — as three different stages:
- What a student can do on their own, working independently or without anyone’s help.
- What the student can do with the help of someone.
- What it is beyond the student’s reach even if helped by someone else.
He called the second stage the Zone of Proximal Development (ZPD) which had, as said, two limits: the lower limit, which was set by the maximum level of independent performance, and the upper limit, the maximum level of additional responsibility the student can accept with the assistance of an able instructor. But Vygotsky believed that learning shouldn’t follow development, but rather should lead it. A student should constantly be reaching slightly beyond their capabilities rather than working within them
(Jo Turner-Attwell, 2009).
This reaching beyond one’s capabilities can be pictured as the student entering their Zone of Proximal Development. And this exploration beyond one’s capabilities is not to be made alone, but with an instructor to help in the way. Vygotsky called this instructor the More Knowledgeable Other (MKO), the role of which is to help the student throughout their ZPD by scaffolding the path they have to follow to learn how to solve new problems.
The Personal Learning Environment and the Zone of Proximal Development: a static approach
The Personal Learning Environment could be understood both as the Zone of Proximal Development and the full set of More Knowledgeable Others, understanding by More Knowledgeable Others not only as people of flesh and blood, but any kind of knowledge construct that we can imagine: from the more typical teachers and open educational resources to all sorts of digital content including messages in fora, multimedia files and so on. As Graham Attwell (2010) puts it, the MKO can also be viewed as a learning object or social software which embodies and mediates learning at higher levels of knowledge about the topic being learned than the learner presently possesses
.
But if we really believe that the Personal Learning Environment is much more than a tool but a learning philosophy, there is much more than we can say in the crossroads of the PLE and the ZPD. The Personal Learning Environment is transferring some — or most — of the responsibility of somebody’s learning path from the instructor (back) to the learner. And, in doing so, it also implies regaining the control of one’s own learning path and its design. In relationship with the Zone of Proximal Development:
The role of a Personal Learning Environment may be not only that of a tool to provide access to ‘More Knowledgeable Others’ but as part of a system to allow learners to link learning to performance in practice, though work processes. And taking a wider view of artefacts as including information or knowledge accessed through a PLE, reflection on action or performance may in turn generate new artefacts for others to use within a ZPD (Graham Attwell, 2010).
The Personal Learning Environment and the Zone of Proximal Development: a dynamic approach
All these reflections stand for a static approach to the Zone of Proximal Development, that is, at a given time and at a given place. Indeed, in Vygotsky’s time, the boundaries of the ZPD were indeed very physical: the evolution of a wood carver’s craftsmanship was bound by the availability of master craftsmen and the possibility to be an apprentice in a nearby workshop.
But Information and Communication Technologies have capsized the whole previous scenario and, thus, the relationship between Personal Learning Environments and the Zone of Proximal Development should be approached not only within the state-of-things prior to the Internet, but also in how this state-of-things is shifting forward.
Thus, one way to look at the ZPD-PLE relationship is seeing the PLE as a way to build, fill in with or reach out for the tools and people that will help a learner through the ZPD. Another way to look at the ZPD-PLE relationship is how the PLE (re)defines the ZPD itself, continuously, dynamically.
Unlike in a world without digital access to information and communications, in a digital world content and people are available all at once. Maximalistically speaking, a PLE can be conformed by virtually everything that exists out in the cyberspace. If virtually everything is at reach, virtually everything can be understood as the more knowledgeable other. With a full, total, comprehensive access to the more knowledgeable other there virtually is no upper limit of the Zone of Proximal Development, there virtually is no level of problem solving that is unreachable for the student.
The PLE, has then two roles in relationship with the ZPD:
- It helps in building the inner structure of the ZPD, its components.
- It helps in building the outer structure of the ZPD, its boundaries.
There is a sort of corollary to the previous second statement. In Vygotsky’s time, learning — and hence the ZPD — was sort of linear: woodcarving apprentices would move “up” to a new master craftsman once they had mastered some skills themselves with the help of their previous/actual master. Progress would end when there were no more master craftsmen around whom to learn from. On the other hand, learning face to face with a human more knowledgeable other meant not only that one had to “use them up” but that one could not “consume” any other more knowledgeable others: learning was unidirectional, linear.
When MKOs are conformed by all kind of tacit and explicit knowledge constructs in one’s PLE, there is no way of (a) “using them up” and (b) not being able to move in parallel with more than one more knowledgeable other. We can then think of the PLE both as the biggest ZPD possible, or as the overlapping of different snapshots of a PLE that evolves “fractalically”, multidirectionally, on time, on demand, until it (potentially) covers the whole cyberlandscape.
The future of educators?
One of the conclusions that one might infer from the previous statements that they are proof of the postulates from thinkers like Syemour Papert, Roger Schank or Nicholas Negroponte: in a digital world, all you have to do is build a PLE as big as the biggest imaginable ZPD. Imagine all you need to learn and it already is out there.
I personally do not agree with that thesis. If PLEs can be understood from a dynamic point of view and work well for all your life-long learning and corresponding ZPDs, it is also true that, from a static point of view, they need to be built to scaffold your way through a specific ZPD. And it is in this scaffolding that help is required.
In other words, and summing up, I believe that it is likely that we see a decreasing need of instructors as more knowledgeable others in order to learn something, but an increasing need of instructors as more knowledgeable others in order to learn how to learn something. With Personal Learning Environments to cover the ground of one’s Zone of Personal Development, learning how to learn, how to design one’s own learning process may be more relevant than ever and require more help from third parties. This is, I think, the most promising future of teaching today.
UPDATE: A more elaborated version of this article was published in an academic journal as it appears below. Follow the link for a full-text download:
By Ismael Peña-López (@ictlogist), 10 July 2012
Main categories: Cyberlaw, governance, rights, e-Government, e-Administration, Politics, Information Society, Meetings, News
Other tags: idp, idp2012
No Comments »
The proceedings of the 8th International Conference on Internet, Law & Politics (IDP 2012): Challenges and Opportunities of Online Entertainment. will be free for download in the following days on this page.
Content, besides some minor editing, has followed the originals, so the reader will find both articles in Spanish or English.
To cite this works use, please, any of the following references:
Cerrillo i Martínez, A., Peguera, M., Peña-López, I., Pifarré de Moner, M.J., & Vilasau Solana, M. (coords.) (2012). Retos y oportunidades del entretenimiento en línea. Actas del VIII Congreso Internacional, Internet, Derecho y Política. Universitat Oberta de Catalunya, Barcelona 9-10 Julio, 2012. Barcelona: UOC-Huygens Editorial.
Cerrillo i Martínez, A., Peguera, M., Peña-López, I., Pifarré de Moner, M.J., & Vilasau Solana, M. (coords.) (2012). Challenges and Opportunities of Online Entertainment. Proceedings of the 8th International Conference on Internet, Law & Politics. Universitat Oberta de Catalunya, Barcelona 9-10 July, 2012. Barcelona: UOC-Huygens Editorial.
8th Internet, Law and Politics Conference (2012)
By Ismael Peña-López (@ictlogist), 10 July 2012
Main categories: Cyberlaw, governance, rights, e-Government, e-Administration, Politics, Information Society, Meetings
Other tags: antonio_troncoso, esther_mitjans, idp, idp2012, jose_luis_piñar_mañas, maria_gonzalez
No Comments »
Panel on Privacy On Line
Chairs: José Luis Piñar Mañas. Professor of Administrative Law. Vice-Chancellor of International Relations at CEU San-Pablo University (Madrid). Former Director, Spanish Data Protection Authority..
Antonio Troncoso Reigada. Professor of Constitutional Law. Former Director, Data Protection Authority of the Region of Madrid.
The Internet has a huge potential for participation, especially social media. Freedom of expression has found a perfect platform on the Internet. Thus, minors have not to have their access to the Internet or social networking sites forbidden.
The proliferation of barriers for data protection is creating too many problems for the evolution of the Internet: we need a harmonization of law, not only within the EU but worldwide. Especially now that cloud computing is becoming mainstream.
The regulation framework in the EU is becoming better, but there is a certain lack of democracy, a lack of political and public debate on the issue.
Esther Mitjans. Professor of Constitutional Law, University of Barcelona. Director of the Catalan Data Protection Authority.
In the Internet age, privacy is a very important matter, present everywhere. There is a need for risk management, as these are new territories with new practices that bring with them plenty of risks and hazards. Behaviours of people cause not only risks upon themselves but also upon third parties. Data protection is about the crossroads of all these risks and practices. And we do not have to forget that the Internet does not believe in boundaries, borders and frontiers.
María González, Head of Legal for Spain, Portugal & Greece at Google.
The problem of short-term regulation can affect innovation, economic growth and the evolution of the Internet as a communication (not only business) platform.
Concerning cookies, the industry is now trying to decide what is the best design for opting-in concerning tracing cookies, and that the user is empowered with the control of their own data and privacy.
Regulation has to be based on transparency: all practices related to data protection, public, private and corporate have to be transparent and accountable.
The “physical” location of data is totally irrelevant when they are constantly replicated and transferred. Thus, what matters is demanding liability and responsibility to the firm, but not that these data are kept on a closed box in a specific territory or jurisdiction.
8th Internet, Law and Politics Conference (2012)
By Ismael Peña-López (@ictlogist), 10 July 2012
Main categories: Cyberlaw, governance, rights, e-Government, e-Administration, Politics, Information Society, Meetings
Other tags: andrew_mcdiarmid, christopher_marsden, fernando_galindo_ayuda, idp, idp2012, laszlo_nemeth, maria_gracia_procedda
No Comments »
Communications on Government and Regulatory Policies
Chairs: Agustí Cerrillo Martínez, Senior Lecturer and Dean of the School of Law and Political Science of the Universitat Oberta de Catalunya (UOC).
Guiding Principles for Online Copyright Enforcement.
Andrew McDiarmid, Senior Policy Analyst, Center for Democracy & Technology, Washington, DC (USA); David Sohn, General Counsel, Center for Democracy & Technology (USA).
Since the 2008, in the US there has been a pro-intellectual property regulation process, establishing the IP enforcement coordinator and increasing the resources for government enforcement. Principles for a balanced copyright enforcement:
- Target true bad actors.
- Preserve safe harbours.
- Study the costs and benefits.
- Voluntary initiatives must respect consumer interests.
- Set realistic goals.
- Education and lawful options are essential.
Domain Name-focused enforcement is a blunt instrument: entire sites are affected, including other sites. There are workarounds and it violates safe harbour cases. There is a harm to free expression due to overbreadth. There are risks of evasion.
Internet Co-Regulation and Constitutionalism.
Christopher T. Marsden, Director of the Essex Centre for Comparative and European Law. Senior Lecturer, Essex School of Law (UK).
Regulation:
- Statute backed code, appointed by the Government. Threat of regulatory intervention.
- Approved code, regulated by an independent body. Treat of sanctions.
- Industry code, set by the industry associates. Industry self-interest.
- Unilateral code, set by service providers. Individual self-interest.
Co-regulation (the independent body’s) is more interesting than statutory regulation or self (industry & unilateral) regulation, which are, notwithstanding, the ones that are more common.
Co-regulation says that civil society, the people, should have a formal role in it: multistakeholder-isation, it is a process and not a static model, e.g. the ICANN. This is yet to be enforced by governments and courts.
We need movement towards formal recognition and formalisation of co-regulation: Legislation 2.0
Electronic Democracy, Internet and Governance. A concretion.
Fernando Galindo Ayuda, Catedrático de Filosofía del Derecho, Universidad de Zaragoza.
Access to information: conscious participation of citizens over a specific matter. Governance as politics: the art of ruling in the pursuit of public well-being. The Internet is certainly boosting communication, but is it fostering democracy?
Reviving privacy: the opportunity of cyber-security.
Maria Grazia Porcedda, Research assistant, Department of Law, European University Institute, Florence (Italy).
What is cybercrime?
- Crimes against availability, integrity and confidentiality of computer systems: illegal access and hacking, illegal interception, data interference (malware, botnets, trojans), system interference (DoS, DDoS).
- Computer related: forgery, fraud.
- Content-related crimes: child pornography.
- Copyright infringement.
There are different notions of security and privacy, depending on where the weight is put between privacy and security and what is the approach towards cybercrime. But we can integrate de facto security and privacy. Cybersecurity is about protecting privacy, both by passive measures taken by educated users and by active measures against cybercrime.
PIPA, SOPA, OPEN — The end of piracy or privacy?
László Németh, PhD Student, Institute of Comparative Law, Faculty of Law, University of Szeged (Hungary).
PIPA and SOPA are similar in many ways: against foreign (rogue) sites, domain name seizure, in personam, in rem action, presumption of guilt, voluntary action, etc.
PIPA and SOPA have raised concerns, objections and even protests.
The OPEN act demands the web to be kept open.
We surely now need new global treaties (WIPO, WTO), and in the makings of these treaties the users should be asked for their opinion. Of course, one of the problems of “asking the users” is how to find valid interlocutors. The website KeepTheWebOpen.com includes the feature of commenting on the OPEN Act.
8th Internet, Law and Politics Conference (2012)

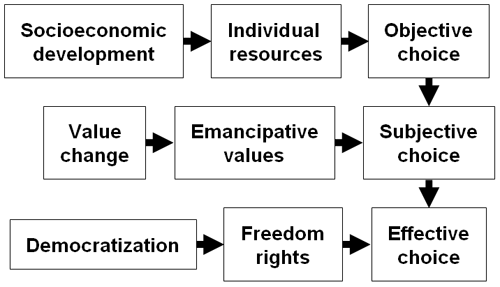 The concept of human development
The concept of human development